
Key Recommendations to Help Mitigate Ransomware
Ransomware and Cyber Attacks — insider, outsider and even nation-state sponsored — threaten business operations and for many organizations, ransomware had greatly impacted ability to operate. With reputation customer and confidential data, money and time on the line, how will you protect against incoming threats?
Multi-State Information Sharing and Analysis Center (MS ISAC) defines ransomware as a type of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption, putting organizations under duress while they recover from the cyberattack and re-assess their security measures.
To understand what ransomware is and how to reduce the potential from being a victim, Red River Cyber & Risk Management Practice Lead Robert Allende breaks down the steps to take in developing a strong defense against incoming cyber threats. With years of working with customers from large enterprises of various sizes, Allende has seen many businesses be unprepared for the massive increase in ransomware attacks. In his experience, customers are susceptible to ransomware in a number of ways – phishing attacks, identity thefts, malicious URL’s and compromised attachments, poor patch management, allowing backdoor access to applications, lack of end user security training and more.
Allende explains that the best place to start is by performing an overall ransomware risk assessment specific to your organization, reviewing cyber insurance plans and identifying limits and steps the provider will take in the event of an impactful ransomware event then developing a prioritized action plan on remediation and incident response efforts. In addition, an organization must take pro-active measures via defined use cases & simulated attack scenarios do plan for what can happen after an incident outline recovery options in the event of a cyberattack.

Increase Protection & Reduce Ransomware
While there are many tactics that can be used, here are some key recommendations to increase your protection and reduce probability against ransomware:
- Stay current and employ the use of advanced email security tools. Based on experience, advanced email security tools are the some of the most effective places to start when it comes to defending against the early stages of bad actor advanced malware and ransomware deployments.
- Enable employees with awareness training coupled with quarterly measurement testing programs. Helping employees increase their awareness of cyberthreats is paramount to helping an organization stay safe from ransomware. To help combat the ransomware threat, Allende suggests formalizing a phishing and user training awareness program to educate employees on social engineering and to give them defensive strategies to implement in their email, mobile and texting communications. In addition, it is imperative the training program utilize quarterly training effectiveness testing for the first year then biannual testing afterwards to ensure the email safety and phishing protection are making a positive impact.
- Document, backup and test your critical digital assets. The importance of proper documentation and reporting cannot be stressed enough, he explains. Organizations that want to stay on top of incidents will document all known assets – physical, network, virtual and critical digital (data) – which will be especially helpful if a third-party incident support or law enforcement is involved.
- Patch & Supply Chain Management. Security patch management is the process by which an organization secures existing software, computers and technology systems to mitigate known security vulnerabilities. These vulnerabilities are often due to a compromised gateway that an attacker has used to deliver or exploit malware. Releasing patch management updates can also be tricky as organizations can be tricked into downloading false patches that often result in malware. The criticality of testing and using verified sources cannot be emphasized enough when it comes to maintaining quality cyber hygiene, as many cyber threats like ransomware attacks could have been prevented by applying the latest software patch.
- Implement Quality Managed Detection and Response (MDR) program. The main benefit of a strong Managed Detection and Response platform or service is that it helps rapidly identify and limit the impact of threats without the need for additional staffing. In Allende’s career, he has found that finding the right combination of technology and human expertise to perform threat hunting, monitoring and response is crucial for any business to improve their security posture and become more resilient to potential attack. Protecting all the endpoints with a quality MDR program is especially important for remote users, as traffic patterns have changed over the past 18 months.
- Develop a functional incident response plan. To ensure that you have a valid incident response plan (IR) customized to your specific needs, Allende recommends utilizing sources such as the website Stop.Ransomware.gov as well as NIST’s IR 8374 plan, the MS – ISAC website or the SANS Incident response framework. Creating and testing an effective incident response plan ensures that key stakeholders are aware and involved in the IR program as it develops.
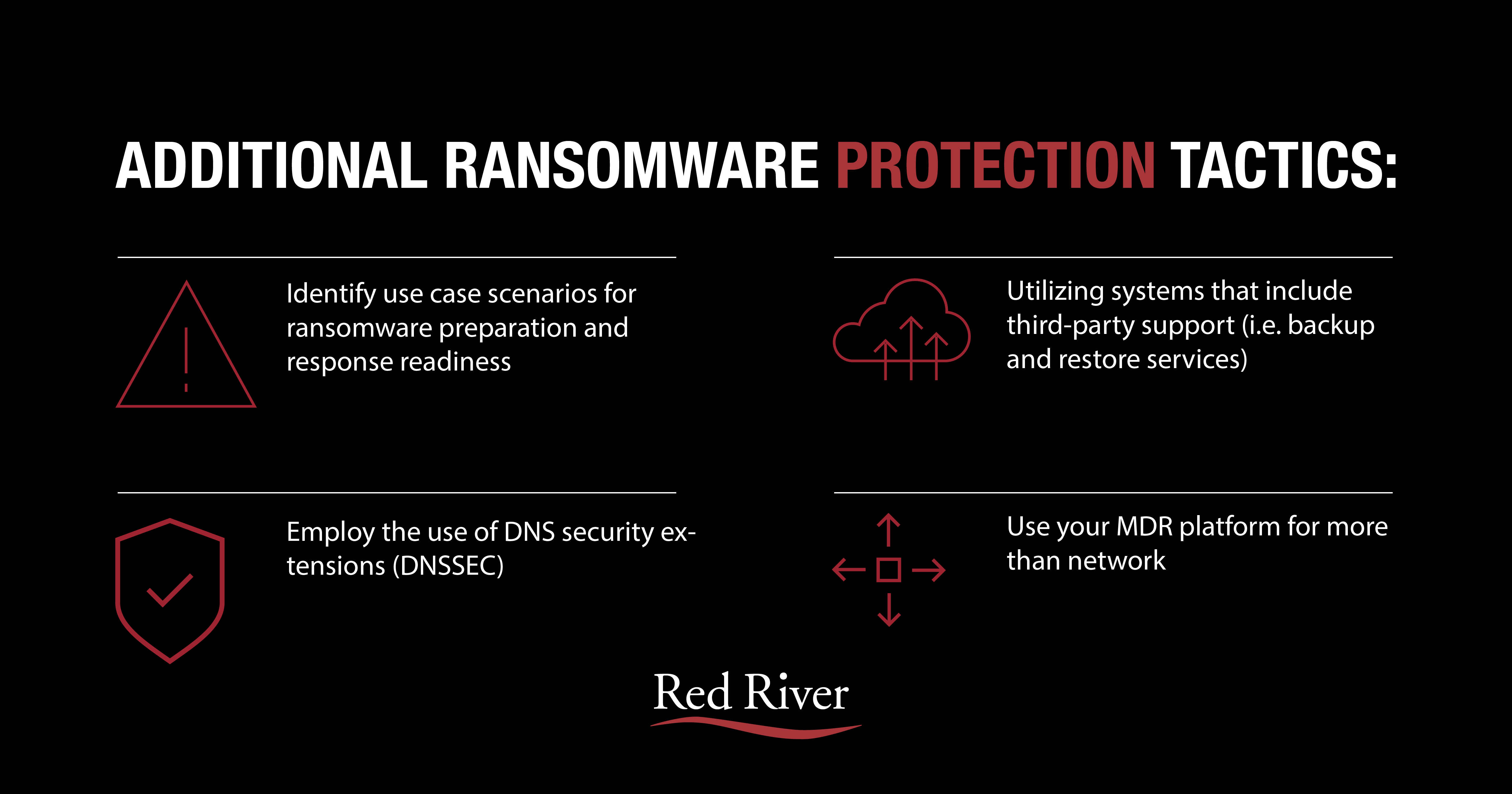
Additional Ransomware Protection Tactics
For organizations wishing to extend their cyber protection, here are some additional technical threat prevention items to consider:
- To increase your cyber team’s efficiency, identify use case scenarios for ransomware preparation and to improve response readiness. By detailing use case scenarios prior to incidents caused by malware attacks, you are enabling your team to be ready for any ransomware threat.
- To better protect your external network connectivity, employ the use of DNS security extensions (DNSSEC) to authenticate DNS responses with the major goal of preventing spoofing, which often leads to malware. DNSSEC works to protect networks from ingesting fake DNS data by using public key cryptography to digitally sign authoritative zone data when it comes into the system and then validating when the data reaches its destination.
- To prevent malware from entering your supply chain, utilize security assessment and systems that cover third-party support. Using security assessment and systems critically improves your chances at stopping malware from infiltrating your organization’s supply chain.
- To increase your MDR platform, go beyond network visibility. Your security operations center should increase coverage to include endpoint security and risk management, the results of which can be utilized to improve business operations while defending against ransomware and related cyberattacks.
Mitigating the threats and risks associated with ransomware can be daunting. With assistance from technology transformation companies like Red River, businesses of all sizes can increase their disaster preparedness and improve their readiness to ransomware attacks, should they arise. Protecting your business starts with protecting your data. Preparation and response planning is the key as it’s not a matter of you will be attacked, it is a matter of when and if you will be ready when that happens.
ABOUT RED RIVER
Red River brings together the ideal combination of talent, partners and products to disrupt the status quo in technology and drive success for business and government in ways previously unattainable. Red River serves organizations well beyond traditional technology integration, bringing 25 years of experience and mission-critical expertise in security, networking, analytics, collaboration, mobility and cloud solutions. Learn more at redriver.com.

written by
Red River
We call ourselves a technology transformation company because we know how to harness the power of technology to change the way you do business and meet mission objectives. Our industry leading technical expertise, strategic partnerships and portfolio of services and solutions that span the entire lifecycle of technology have made us the partner of choice for clients in the commercial, federal and SLED markets interested in optimizing business processes and maximizing the value of their investments. Learn more about Red River.




