
First Steps Implementing Zero Trust
Zero Trust is everywhere: the media, your management, 160+ OEM’s who propose some form of a Zero Trust solution, government standards and now Presidential mandates. The need is genuine, the question I propose is, “Are you ready?”
Zero Trust Defined
Zero Trust is a security model based on the principle of maintaining strict access controls and not trusting anyone by default, even those already inside the network perimeter. Zero Trust removes implied access and only grants trusted users the access they need to perform the job or work role. Zero Trust is a methodology, not a product.
Fundamentally, a Zero Trust approach uses a holistic view and as such there is no specific infrastructure implementation or architecture that provides a single and complete Zero Trust solution.
As a reference model, take a look at the NIST Special Publication 800-207. This is a “standard” Zero Trust conceptual framework to help illustrate the components listed in a typical ZTA framework and functional capabilities.
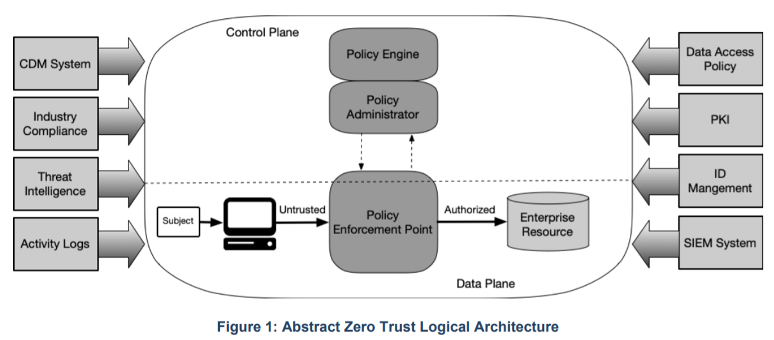
There are also OEM-specific solutions (I will cover more below), industry analyst architectures (Forrester, Gartner, various market reports, etc.)
Adding to the ZT alphabet soup there is a growing direction titled as Zero Trust Enterprise (ZTE): practical access management method and technologies used to enable Zero Trust thinking. ZTE is a blending of existing access management tools, managing implicit vs. untrusted access while overlaying updated ZT tools into a real-world ZT architecture vs. a wholesale uplift to become Zero Trust ready.
Enabling Your Zero Trust Architecture Journey
With all the Zero Trust options on the table, where do you begin? There are many business reasons, technical articles and cyber security risk management justifications on “Why” to implement Zero Trust Architecture. Here are 5 practical steps (often no cost) you can take on “How” to begin your Zero Trust Journey:
- Embrace Zero Trust: Zero Trust has moved beyond a buzzword and is a mainstream cyber security strategy, OEMs are meeting with C-level groups to discuss Zero Trust and just about every main cybersecurity OEM has a component. On May 12 2021, President Biden announced the U.S. Cyber Security Executive Order, requiring agencies to implement a Zero Trust Architecture. Organizational executives are hearing the Zero Trust message from every channel and this will eventually work its way to your desktop. Don’t wait and embrace your appropriate portion of a Zero Trust strategy today.
- Inventory assets, ID critical business workflows, classify based on value: The adage of “you can’t manage what you can’t see” is especially true in Zero Trust. Organizations need to identify all software and hardware assets, capturing base functionality and asset owner. Then create a simple classification process to identify value to the organization (ex: critical; production, and general) with Zero Trust Architecture attributes associated with each classification. Next, understand your organization critical business process and workflows to ensure the supporting assets are protected via the initial Zero Trust Architecture deployment. Take care to assign the identified business and process owners some part in the adoption period, as without their participation this will take much longer to deploy.
- Create a specific plan: Utilize a common Zero Trust Architecture framework or platform approach but make it your own, specific to your organizational security needs. Once you begin, you will quickly be able to define and selectively apply other needs throughout implementation. As I alluded to earlier, there is simply no one-size-fits all strategy.
- Keep it as simple as possible: Less is more. Use the most basic user access right restrictions to begin with and create just three access right groups: critical, production and general. Utilize your inventory sheet from step two, to deploy Zero Trust in phases, prioritize deployment to protect the most critical asset items first based on your organizational needs.
- Communicate the ZTA plan to all employees: Proactively review why the organizations is adopting a Zero Trust framework, including basic training on the concept and why it’s a value to the employee. Cover how they can help, what to expect and why the support is being asked of them to support the program, short and long term. Inclusion will result in a big improvement in rate of adoption and effectiveness.
Utilize Zero Trust OEM Solutions
There are various methods to approach a Zero Trust implementation in terms of architecture, below are a few examples in the state what’s possible and key OEM’s who are proponents of their specific approach:
- Federal ZTA Standard: NIST SP 800-207, the federal standard for Zero Trust. This strategy approach has the upside of a fully structured ZTA implementation but cost, time, resources and ongoing support will be expensive and a heavy lift.
- End-Point Based: Approaches Zero Trust from a user access perspective and security from an end point perspective. Leading OEM example of this is Crowdstrike, partnering with Akamai, Cloudflare, Google Cloud, Okta, Netskope and Zscaler, to provide a comprehensive approach.
- Identity Based: This approach is the core of a true Zero Trust Architecture implementation, utilizing user-based access management, contextual awareness and application access management to deliver a real-time functional solution. Key OEMs in the “ZTA identity based never trust, always verify, enforce least privilege approach” include OKTA, Ping Identity, SecureAuth, Google Beyond Corp, Microfocus & Cyolo for industrial OT networks.
- Application Based: Traditional security models are becoming increasingly irrelevant to today’s decoupled development. An application based Zero Trust solution places key focus on a single strong source of user identity, authorization policies to access an application and access control policies within the application. Leading OEM example of this approach include Cisco Tetration, Ivanti, Auth0, VMware and Microsoft Azure-based services.
- Service & SASE-based: There is a growing tend to integrate Zero Trust and SASE utilizing service-based authentication and verification service to provide secure and verified access. The quick deployment and low cost start up can make this approach a very attractive option. Most often delivered as a cloud-based service approach, service providers in this space include Cato Networks, FireEye / McAfee MVISION & Secure Link.
- Platform-based: The largest and most comprehensive approach is the OEM platform direction. OEMs have committed their “integrated” solution suite ranging from end point to network to policy and management systems. While vendor lock-in is a potential concern most OEMs are including API integration and open systems to allow additional ZTA integration points. Leading OEM’s in the ZTA Platform suite include Cisco, Palo Alto, Fortinet, zScaler, Forcepoint & Microsoft.
Long-Term Considerations
The Zero Trust Architecture and supported OEM solutions will continue to evolve over the next decade. It is my prediction that it will take the next three to five years before the components genuinely settle and services begin to consolidate. There are simply too many moving parts, dynamic IT support components, shifting remote access requirements and evolving threat landscape areas that are moving faster than IT budgets can support. It will take a few in-production Zero Trust Architecture renditions before well-established best practices can be established.
With that as a background, the 160+ OEM solutions plus the ongoing marketing and business pressure to move towards ZTA, the time is now to begin your Zero Trust journey. If you need help getting started, a managed service provider and security expert like Red River can create your customized Zero Trust plan, and help you monitor, manage and implement it.
Top Resource Links
- https://www.darkreading.com/endpoint/the-5-phases-of-zero-trust-adoption?cid=malp&_mc=malp
- https://redriver.com/security/zerotrust
- https://www.whitehouse.gov/briefing-room/presidential-actions/2021/05/12/executive-order-on-improving-the-nations-cybersecurity/
- https://csrc.nist.gov/publications/detail/white-paper/2021/08/04/planning-for-zero-trust-architecture-starting-guide-for-admins/draft
- https://techzone.vmware.com/resource/zero-trust-secure-access-traditional-applications-vmware
- https://www.glocomp.com/implementing-zero-trust-for-the-workforce-ciscos-story/
- https://www.crowdstrike.com/cybersecurity-101/zero-trust-security/
- https://www.paloaltonetworks.com/blog/2021/10/zero-trust-enterprise-in-critical-infrastructure/
Additional Resource Links
- https://redriver.com/security/zero-trust-and-splunk
- https://techzone.vmware.com/resource/zero-trust-secure-access-traditional-applications-vmware
- https://www.cisco.com/c/dam/global/en_ca/assets/pdfs/zero-trust-cisco-connect-vancouver-2020.pdf
- https://www.sdxcentral.com/articles/news/cisco-targets-80b-security-opportunity-doubles-down-on-zero-trust/2021/09/
- https://www.crowdstrike.com/cybersecurity-101/zero-trust-security/
- https://www.paloaltonetworks.com/blog/2020/09/zero-trust-for-iot/
- https://www.paloaltonetworks.com/blog/2021/10/zero-trust-enterprise-in-critical-infrastructure/
- https://events.afcea.org/Augusta20/CUSTOM/pdf/Dell%20Technologies%20-%20ZeroTrust.pdf
- https://www.forbes.com/sites/deloitte/2021/09/20/this-indian-states-response-to-covid-19-could-be-a-model-for-equitable-healthcare/?sh=7a6ded9c6ee1
- https://twitter.com/thinkred/status/1407371549905244163
- https://www.wwt.com/article/how-to-effectively-move-to-a-zero-trust-architecture
- https://statescoop.com/k12-cybersecurity-study-cisa/#:~:text=he%20said.%20%E2%80%9CThat%E2%80%99s-,positive,-.%20The%20threats%20are
- https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf

written by
Red River
We call ourselves a technology transformation company because we know how to harness the power of technology to change the way you do business and meet mission objectives. Our industry leading technical expertise, strategic partnerships and portfolio of services and solutions that span the entire lifecycle of technology have made us the partner of choice for clients in the commercial, federal and SLED markets interested in optimizing business processes and maximizing the value of their investments. Learn more about Red River.




